Splunk Alerts Are Based on Historical Searches Only
A real-time alert cant be set up on a historical search. This isnt so much a stage like the prior ones.
Modify the search to only alert on medium high or critical severities.
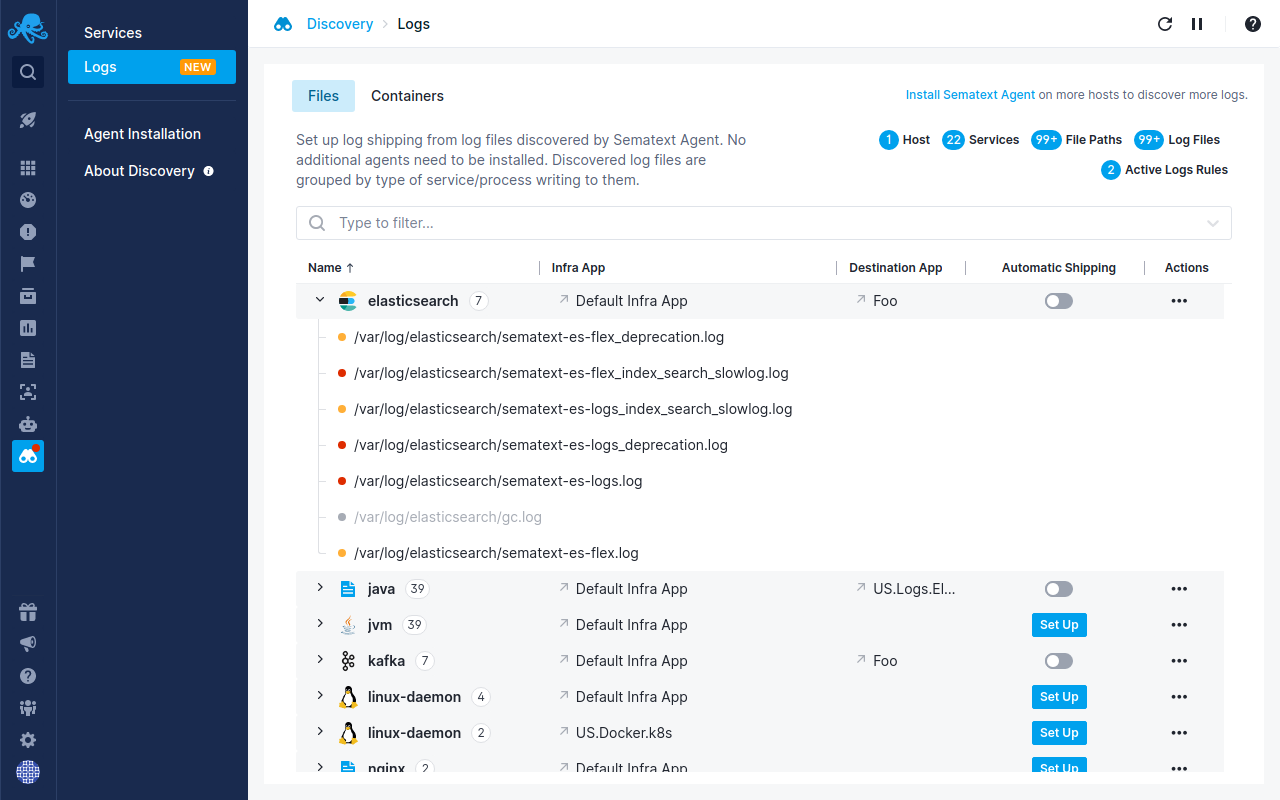
. To specify the period of time over which patterns repeat use the Cycle length parameter. An alert that is based on real-time search. Alerts can be set-up on historical searches to run automatically on regular schedules or when the search results meet specific circumstances.
Splunk alerts can be based on searches that run ______. Especially if you use splunk for PCI compliance having a report showing all alerts fired over a period of time will go a long way to help you satisfy the daily. Splunk alerts are based on historical searches only.
I have splunk logs which will give the ExpiryDate in search result based on the value of the result need to configure an alert before the 10days of expirydate. Displays only events that do NOT contain a value for user. Merely a call out for you to enjoy the fact that your Splunk system now only alerts when something truly needs attention ie.
Splunk alerts are based on historical searches only. Various refer to the READMEmd file for more details. This term differentiates historical searches from real-time searches which run over a window of time.
This alert is based on a real time search which runs overall time. Splunk alerts can be based on search that run_____. This topic shows you how to configure custom alerts and prepare them for use in the Splunk App.
You create an alert by running a search query and saving its result as an alert. Use the Historical Anomaly alert condition to monitor metrics with patterns that repeat over known fixed periods of time. The searches generate notable events based on various situations occurring with services KPIs and entities.
If you want to search on a field click the Fields tab enter the field name then press Enter. A real-time alert is _____ constantly running in the background. Splunk alerts can be based on searches that run _____ 1.
Historical Anomaly alerts when a signal is different from the same periods in the past for cyclical or seasonal data. This is where we can use streamstats to calculate the threshold based on the last 30 days for any given hour. You can easily build a report based on the results of this search.
We know that we can create different knowledge objects in Splunk like Dashboards Alerts Reports etc. This correlation search will find Splunk events with the following characteristics. A searchthat has a distinct time range such as the past hour the previous day or between 2 and 4 last Tuesday.
To continue adding keywords or fields to the search click Add Filter. 12-28-2019 Thanks in Advance. It is for informational purposes only and shall not be incorporated into any contract or other commitment.
Alerts can be based on a wide range of threshold and trend-based scenarios including empty shopping carts brute force firewall attacks and server system errors. It runs periodically with a set schedule. I am excluding summary_index alert actions since I am only interested in real alerts and not summary index searches.
Splunk alerts are actions which get triggered when a specific criterion is met which is defined by the user. A real-time alert is __________. C displays only events that do NOT contain a value for user.
Sending Multiple Alerts Based Upon Multiple Conditions Using One Alert In Splunk. There are mainly three types of alerts available in Splunk. Running a scheduled saved report _____.
Historical searches usually review data in the past but you can set up these searches to review events with future-dated timestamps if your index contains them. To search on a keyword click the Keyword tab type the keyword or phrase you want to search on then press Enter. Congratulations and get ready for your promotion.
Splunk result will be. The Splunk App for Unix and Linux comes with twelve alerts which you can configure in the Settings. Splunk Splunk Turn Data Into Doing The Engine for Machine Data Splunk Cloud.
Splunk undertakes no obligation either to develop the features or functionalities described or to include any such feature or functionality in a future release. On a regular schedule 2. Returns a fresh result set.
Splunk supports three types of alerts. On a regular schedule. If you want you can add custom alerts by saving searches and adding specific parameters to make them also appear in the Settings.
A True b False. SearchHeadLevel - Search Messages admins only this alert searches the splunk search messages but is designed to find errors that cannot be fixed by end users generic alert Updated alerts. Select all that apply a in real-time b on a regular.
Using the same search to calculate the alert volume for the whole 30 days the threshold will be based on historical current and future data for any given hour but the last. When running a correlation search the threshold is based on historical data. Historical searches provide a static snapshot of events at a given time.
It is an alert that is based on a historical search. The Timeline and Logs table now display only the log events that. The goal of alerts can be logging an action sending an email or output a result to a lookup file etc.
See this solution on Splunk Answers for more information including how to change your search to a real-time search if thats what it should be. Constantly running in the background. Youre trying to set up a real-time alert from a historical search.
But we will talk about new and interesting tricks regarding alert.
Index Management Elasticsearch Guide 7 17 Elastic
Ilm Manage The Index Lifecycle Elasticsearch Guide 8 1 Elastic

Understanding And Baselining Network Behaviour Using Machine Learning Part Ii Splunk
Reactive To Proactive Intelligent Troubleshooting And Monitoring Wit

10 Best Log Analysis Tools Of 2022 Free Paid Log Analyzers Sematext
Reactive To Proactive Intelligent Troubleshooting And Monitoring Wit
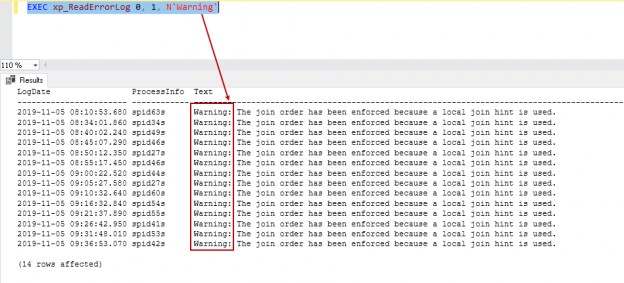
Read Sql Server Error Logs Using The Xp Readerrorlog Command
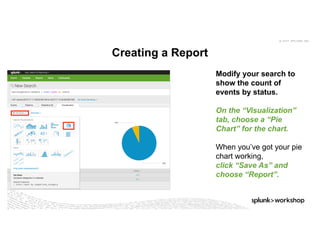
Reactive To Proactive Intelligent Troubleshooting And Monitoring Wit
How To Get Started With Asana Goals Product Guide Asana

Manage Notification Subscribers Splunk Observability Cloud Documentation
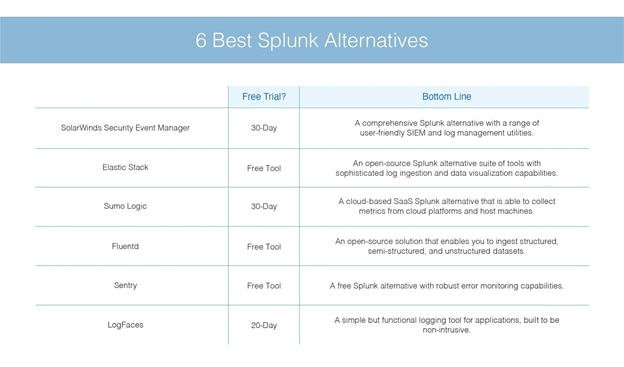
6 Best Splunk Alternatives For Log Analysis Monitoring Dnsstuff
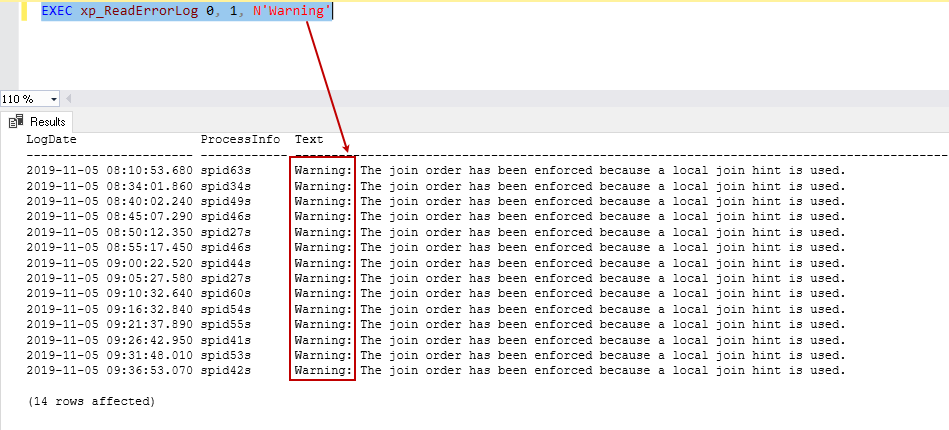
Read Sql Server Error Logs Using The Xp Readerrorlog Command

Reactive To Proactive Intelligent Troubleshooting And Monitoring Wit
Reactive To Proactive Intelligent Troubleshooting And Monitoring Wit

Understanding And Baselining Network Behaviour Using Machine Learning Part Ii Splunk


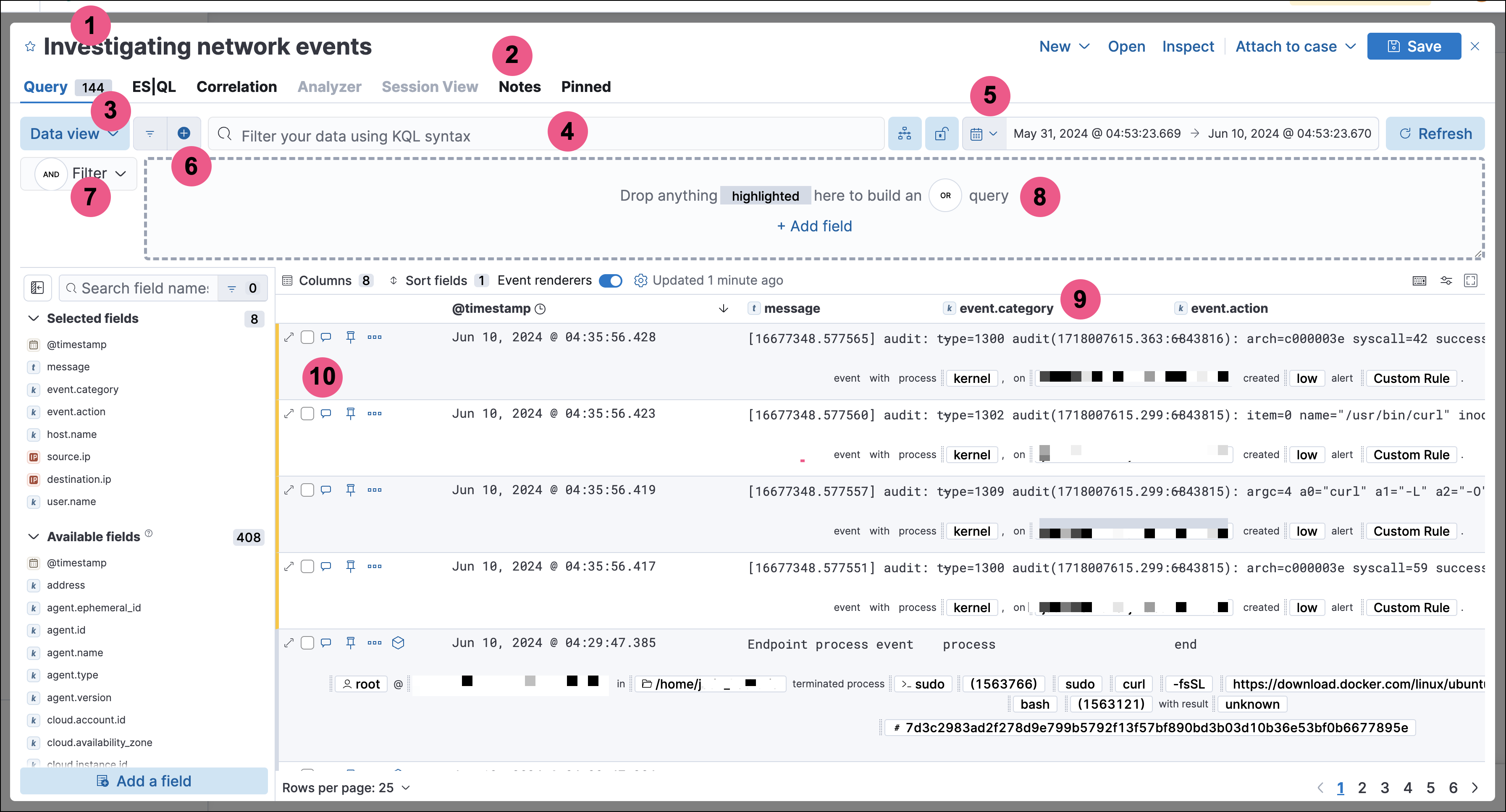

Comments
Post a Comment